As I finished Jamf 100, I started my journey towards Jamf 170 and hopefully Jamf 200 which I am asking my IT job to pay for me. Before I go to the topic, I would like to briefly recap what I learned in Jamf 100.
The first section was a general and basic overview of macOS and mobile devices such as storage, file system and app management which I mostly knew. The only new thing for me was that there are 5 volumes by default in macOS: data, system, preboot, virtual memory and recovery. The second section moved into introduction to Jamf Pro which I was familiar with from my Computer Support Specialist role as I had to do a lot of tasks with Jamf Pro. I learned that Apple School or Business Manager plays important role in device management. I also learned that Jamf Pro send commands through Apple Push Notification. I got a good glance at automatic enrollment vs user-initiated enrollment. This leads me to section three where I grasped groups, advanced searches and configuration policies while section four focused mainly on policies. The key difference between a policy and configuration profile is that policy uses binary stored on user’s machine to execute a payload instead of APN (Apple Push Notification). Ok, let’s get started into Compliance Benchmark for macOS!
Compliance benchmarks are specific recommendation or rules concerning security of a device. In this simple lab, I would like to use Jamf Compliance Editor to import them into Jamf Pro. The compliance pdf is in CIS website ready for download in case I need to review that.
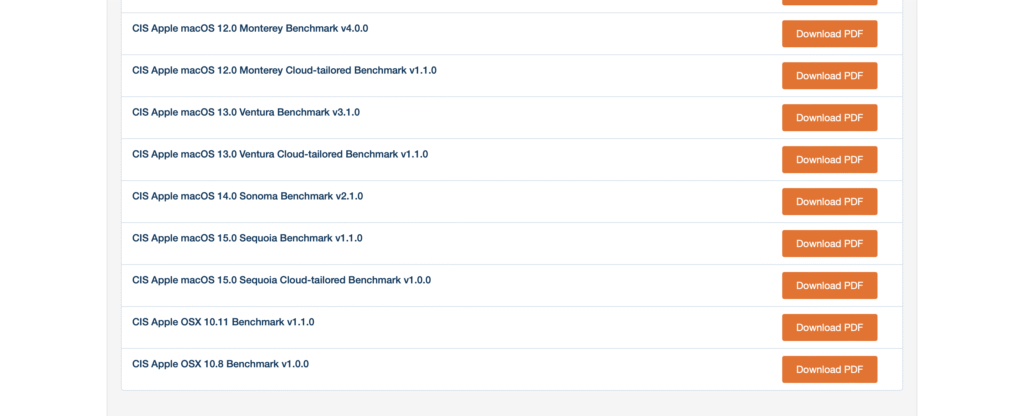
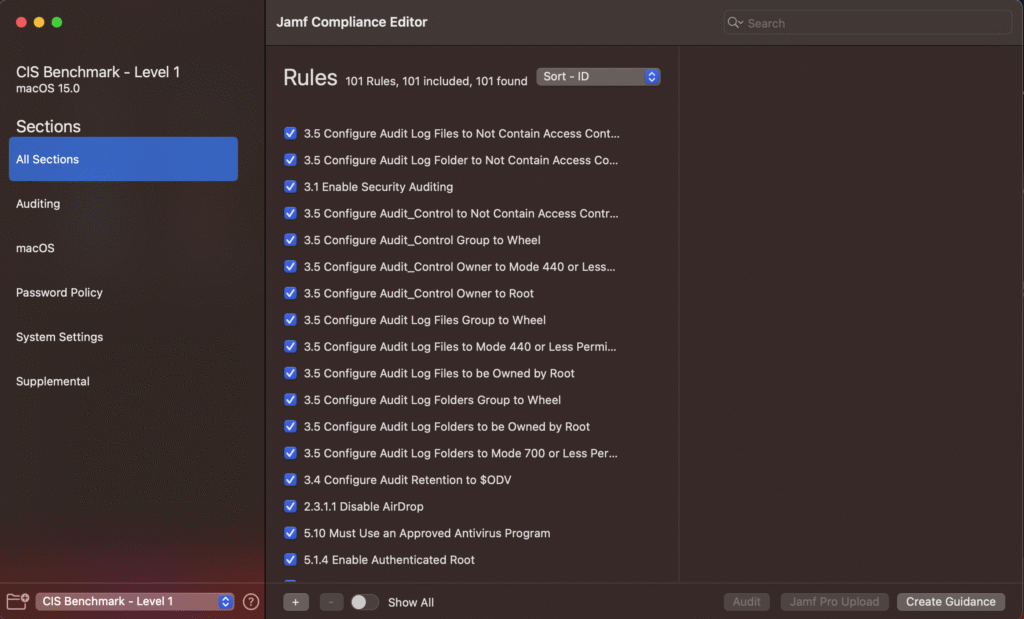
Next, I am going to get Jamf Compliance Editor. Suppose my supervisor said to comply all devices with Level 1 compliance of CIS.

And I have got them here
If I go to password policy, I see
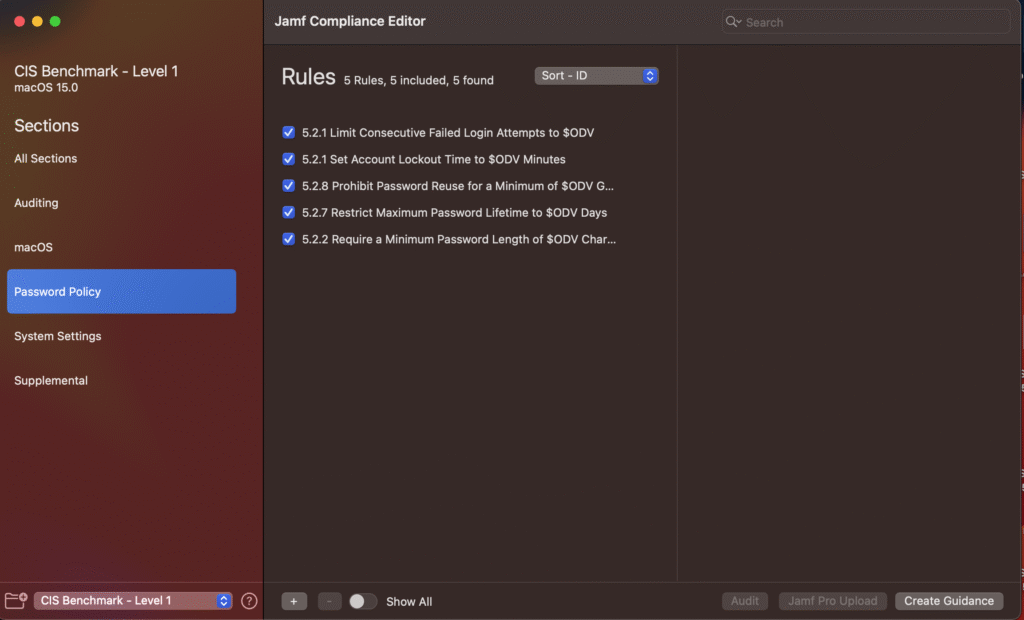
There are $ODV which means they are Organizational Defined Values and need to be set by me. Here, I can configure some of the policies
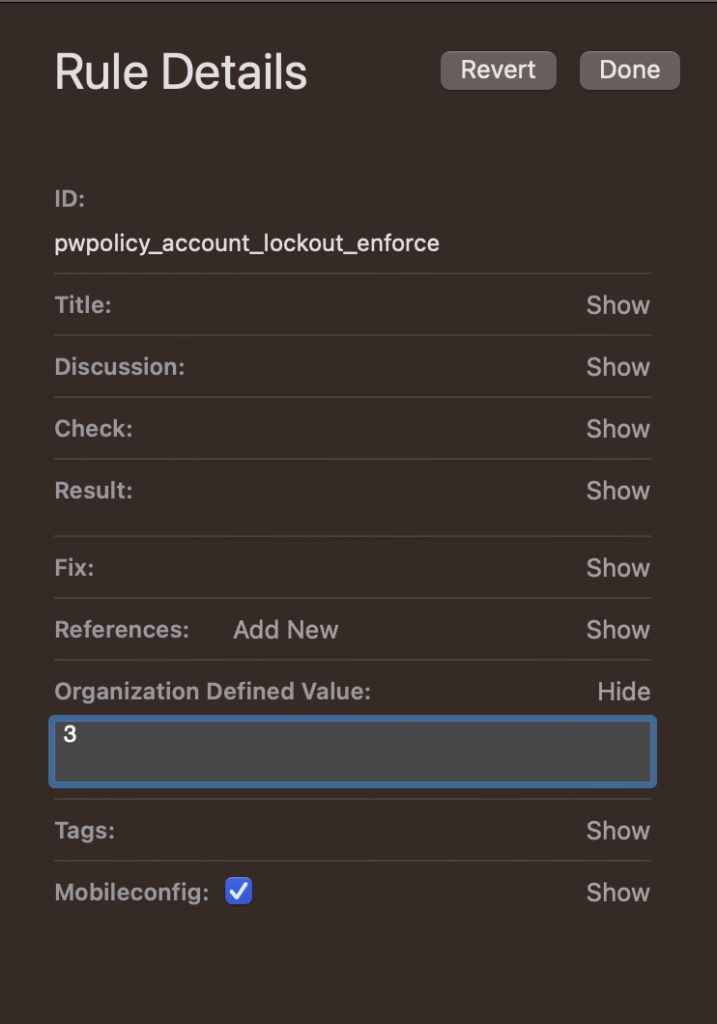
Above I am defining account lockout time to 3 from 5 which was default. Jamf recommends to keep default values perhaps because Level 1 are essential, practical security tips. It makes sense what jamf is telling; however, organization’s security baseline can differ significantly. In the Jamf Editor, it is possible to include Level 2 security guidelines by clicking “showing all”.
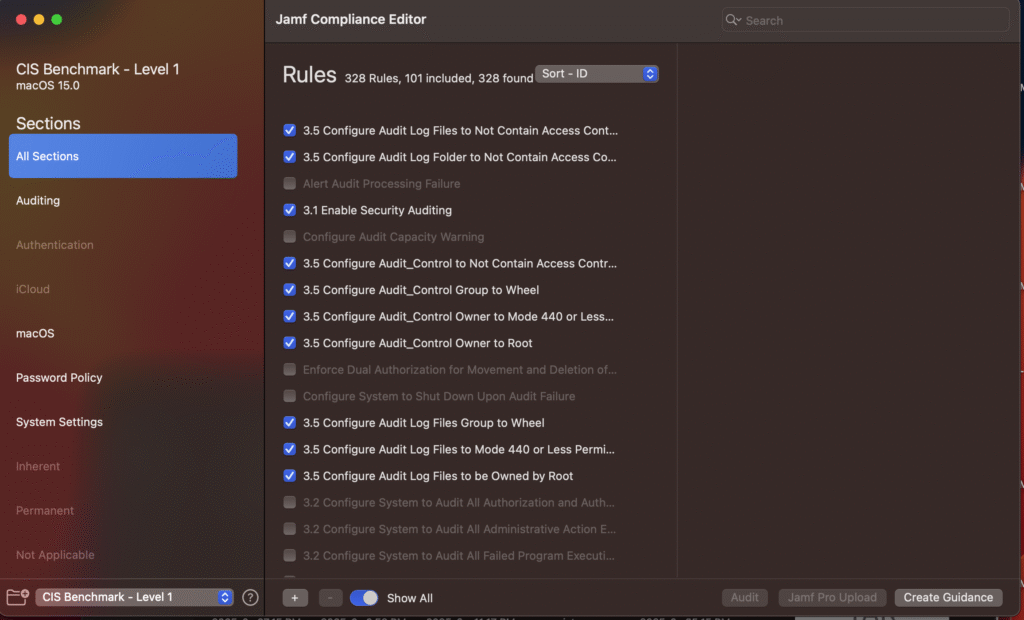
Now, I can customize benchmark for our organization and get a security guideline from Level 2. After choosing my policies for my organization I create the security baseline.
There is a pdf file containing my chosen security rules. To upload this security guideline to Jamf Pro, I simply need to click “Upload to Jamf Pro” button. As for other device management solution, I need to do it manually. In Jamf Pro, it would under Computers -> Configuration Files. The scripts are now ready to be scoped and deployed. In Jamf Protect, this would be under Compliance -> Baseline. The access to Jamf Pro and Jamf Protect are given by an employer and are not available for me at the time of writing.